resources
CIL Security Advisory
Your trusted resource for the latest security updates, threat intelligence, and proactive solutions.

Secure Code Repositories: Protecting Your Source Code from Unauthorised Access
Source code is a plain text computer program written in a programming language to be compiled or assembled. It is…
MAY 28TH, 2025

Open Source Software: How To Secure Them
Open-source software (OSS) is a computer software with publicly accessible source code, meaning anyone can inspect, modify, and distribute it…
MAY 26TH, 2025

Bring Your Own Device (BYOD) Security Risks and Recommendations
BYOD programs present security risks to corporate assets despite offering productivity and flexibility benefits. This advisory outlines these risks and…
MAY 21ST, 2025

Wi-Fi Router Security: The Importance of Changing Your Router’s Default Settings
Wi-Fi routers are the backbone of home and small office networks, connecting multiple devices to the internet. However, many users…
MAY 19TH, 2025

Password Managers: Why Using One Is Better Than Writing Them Down
Managing multiple passwords can be overwhelming, and many users resort to writing them down or reusing the same credentials across…
MAY 14TH, 2025
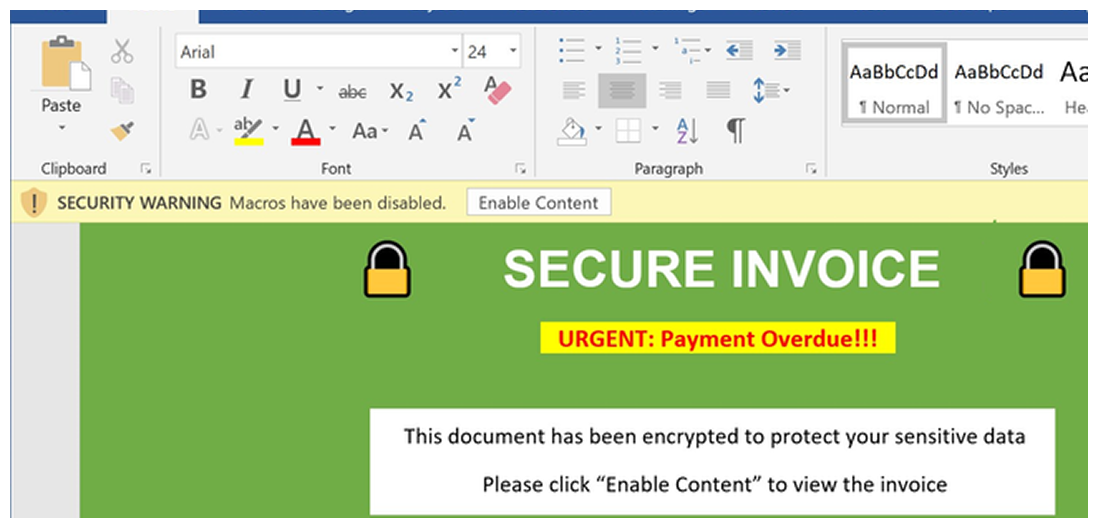
Mitigating Macro Malware Threats in Microsoft Office
Malicious macros in Microsoft Office documents remain a significant cybersecurity threat. Attackers leverage social engineering to trick users into enabling…
MAY 12TH, 2025
Malicious Browser Extensions: Vetting Extensions to Avoid Hidden Malware
Browser extensions are a piece of software that adds new features to your Browse experience and are quite useful and…
MAY 7TH, 2025

Dumpster Diving for Data: Why shredding physical documents is important
In this digital age, it's easy to forget that not all data breaches happen online. One of the oldest and…
MAY 5TH, 2025

Secure Your Wi-Fi Router Now
April 30Leaving your Wi-Fi router in its factory state is a major risk. Cybercriminals scan for routers using default credentials…
APRIL 30TH, 2025
Disclaimer: This publication is provided for informational purposes only and does not constitute professional advice or an endorsement of any specific products, services, or strategies. Readers are advised to use their discretion and seek professional advice before making any business or technology-related decisions based on the information provided.
Never miss a CIL Security Advisory
Stay informed with the latest security updates and insights from CIL.


